⚠️ SCARY Warning: CoinMarketCap HACKED! Your Wallet Could Vanish in 3 Seconds!
CoinMarketCap Security Breach - Verified as TRUE


⚠️ SCARY Warning: CoinMarketCap HACKED! Your Wallet Could Vanish in 3 Seconds!
🚨 EMERGENCY SECURITY ALERT 🚨
Breaking News: CoinMarketCap, the world’s most trusted crypto platform with over 120 million users, has been COMPROMISED! Malicious hackers have successfully infiltrated their system, and your crypto wallet could be completely drained in just 3 seconds!
If you’ve visited CoinMarketCap in the last 48 hours, your wallet might already be at risk. Read this entire guide immediately to protect your assets!

💀 The Nightmare Scenario: How CoinMarketCap Became a Death Trap for Crypto Holders
On June 21st, 2025, the cryptocurrency world woke up to its worst nightmare. CoinMarketCap, the platform that millions of crypto enthusiasts visit daily to check prices and market data, was transformed into a sophisticated phishing trap that could steal everything in your wallet faster than you could blink.
The Devastating Numbers
The attack was discovered when users began reporting a malicious popup appearing on CoinMarketCap’s homepage, innocently asking them to “Verify Wallet”. This seemingly harmless request was actually a sophisticated wallet drainer attack designed to steal every valuable cryptocurrency and NFT from connected wallets.
Timeline of the Attack
🎯 The Anatomy of a Perfect Digital Heist: How the “Verify Wallet” Scam Works
This wasn’t just any ordinary phishing attack. The hackers deployed what security experts call a “wallet drainer” – a sophisticated piece of malicious code that can automatically identify, evaluate, and steal the most valuable assets from your cryptocurrency wallet in a matter of seconds.
How the Attack Works in 3 Deadly Steps
🔬 The Technical Horror: What Makes This Attack So Devastating
Unlike traditional phishing scams that steal passwords or private keys, wallet drainers work by tricking you into signing legitimate-looking blockchain transactions. Here’s what makes them terrifyingly effective:
Automated Asset Detection
The malicious code can instantly scan your wallet and identify:
- High-value NFTs (Bored Apes, CryptoPunks, etc.)
- Rare tokens and altcoins
- DeFi protocol holdings
- Staking rewards and yield farming positions
Lightning-Fast Execution
Once you approve the malicious transaction:
- Assets are transferred in under 3 seconds
- Multiple transactions execute simultaneously
- No time to cancel or reverse the process
- Funds immediately moved to mixing services
The scariest part about wallet drainers is that they use your own wallet’s security features against you. When you see the transaction approval popup, everything looks legitimate – but you’re actually signing away ownership of your most valuable digital assets.
— Blockchain Security Expert, Chainalysis💸 The $100 Million Question: Real Victims, Real Losses
While CoinMarketCap quickly claimed to have “identified and removed” the malicious code, the damage was already done. Security firms estimate that the attack put over $100 million worth of cryptocurrency at risk, with several high-profile victims already coming forward.
Confirmed Victim Reports
Within hours of the attack, several crypto users reported devastating losses:
- NFT Collector: Lost 14 Bored Ape NFTs worth over $1.2 million
- DeFi Trader: $500,000 in various altcoins drained instantly
- Crypto Startup Founder: $125,000 in stETH stolen during “verification”
- Long-term HODLer: 15 years of Bitcoin accumulation – gone in seconds
The attack specifically targeted ERC-20 tokens, which means Ethereum-based assets were at the highest risk. However, security experts warn that similar attacks could easily be adapted for other blockchains including Bitcoin, Solana, and Polygon.
Attack Impact by Asset Type
🛡️ The Heroes Who Saved Millions: How MetaMask and Phantom Responded
While CoinMarketCap initially downplayed the severity of the attack, major wallet providers took immediate action to protect their users. MetaMask and Phantom both deployed their built-in security features to flag CoinMarketCap as a potentially dangerous site.
Automatic Protection Measures
Both wallet providers immediately implemented protective measures:
- Site Blocking: Automatic warnings when users try to connect to CoinMarketCap
- Transaction Warnings: Enhanced scrutiny of any transaction originating from the site
- User Alerts: Push notifications warning users about the security breach
- Emergency Updates: Rapid deployment of security patches to all wallet users
Wallet Provider Response Timeline
This rapid response likely saved millions of dollars in cryptocurrency from being stolen. However, the incident highlights a crucial vulnerability: even the most trusted crypto websites can become dangerous without warning.
⏰ The 3-Second Rule: Why Speed is Everything in Crypto Security
You might wonder why we keep emphasizing the “3 seconds” timeframe. In the world of cryptocurrency security, time is literally money – and 3 seconds is all it takes for a sophisticated wallet drainer to completely empty your digital assets.
The 3-Second Breakdown
Total time from approval to complete asset theft: 3 seconds
This lightning-fast execution is possible because modern wallet drainers use several advanced techniques:
Pre-computed Transactions
The malicious code creates multiple transaction templates before you even connect your wallet, allowing instant execution once approved.
High Gas Fees
Attackers pay premium gas fees to ensure their transactions are processed immediately, jumping ahead of any potential cancellation attempts.
MEV Bots
Sophisticated attackers use Maximum Extractable Value (MEV) bots to guarantee their transactions are included in the next block.
Parallel Processing
Multiple assets can be stolen simultaneously through batch transactions, maximizing the theft in minimal time.
The 3-second window is by design. Attackers know that most users need at least 5-10 seconds to realize something is wrong and attempt to take protective action. By that time, it’s already too late.
— Head of Security, Consensys (MetaMask parent company)🚫 Why Traditional Security Measures Fail
This is why traditional cybersecurity advice doesn’t work in the crypto world. In regular online banking, you might have several minutes or even hours to notice and report fraudulent transactions. With cryptocurrency, once the transaction is confirmed on the blockchain, it’s permanent and irreversible.
What WON’T Save You
- Strong passwords: Irrelevant when you’re tricked into signing legitimate transactions
- Two-factor authentication: Doesn’t prevent wallet drainer attacks
- Antivirus software: Can’t detect legitimate-looking blockchain transactions
- Quick reflexes: 3 seconds is faster than human reaction time
- Customer support: No bank or company can reverse blockchain transactions
This is why the CoinMarketCap hack is so terrifying – it exploited the very foundation of how cryptocurrency works. The attackers didn’t need to steal your private keys or hack your password. They just needed you to approve one seemingly innocent transaction.
⚡ Critical Realization
If you visited CoinMarketCap and saw ANY popup asking you to connect or verify your wallet – even if you didn’t complete the process – your wallet details may have been compromised. The attack code could have been gathering information even from users who didn’t fall for the scam.
Don’t panic – but don’t wait either. In the next part of this guide, we’ll show you exactly how to protect yourself and what to do if you think you might have been exposed to this attack.

7 Critical Warning Signs: Detect Wallet Attacks Before It’s Too Late
URGENT REALITY CHECK: Most crypto holders discover they’ve been hacked only AFTER their funds disappear. The average detection time? 72 hours – far too late to save your assets. But what if you could spot the warning signs within the first few minutes?

The harsh truth about crypto security is that prevention is everything. Once your private keys are compromised, there’s no “undo” button, no customer service to call, and no insurance to cover your losses. This is why recognizing early warning signs can mean the difference between keeping your fortune and losing everything.
Warning Sign #1: Unexpected Wallet Connection Requests
Red Flag Example: You visit CoinMarketCap as usual, but suddenly see a “Verify Your Wallet” popup that wasn’t there yesterday.
Warning Sign #2: Browser Security Alerts

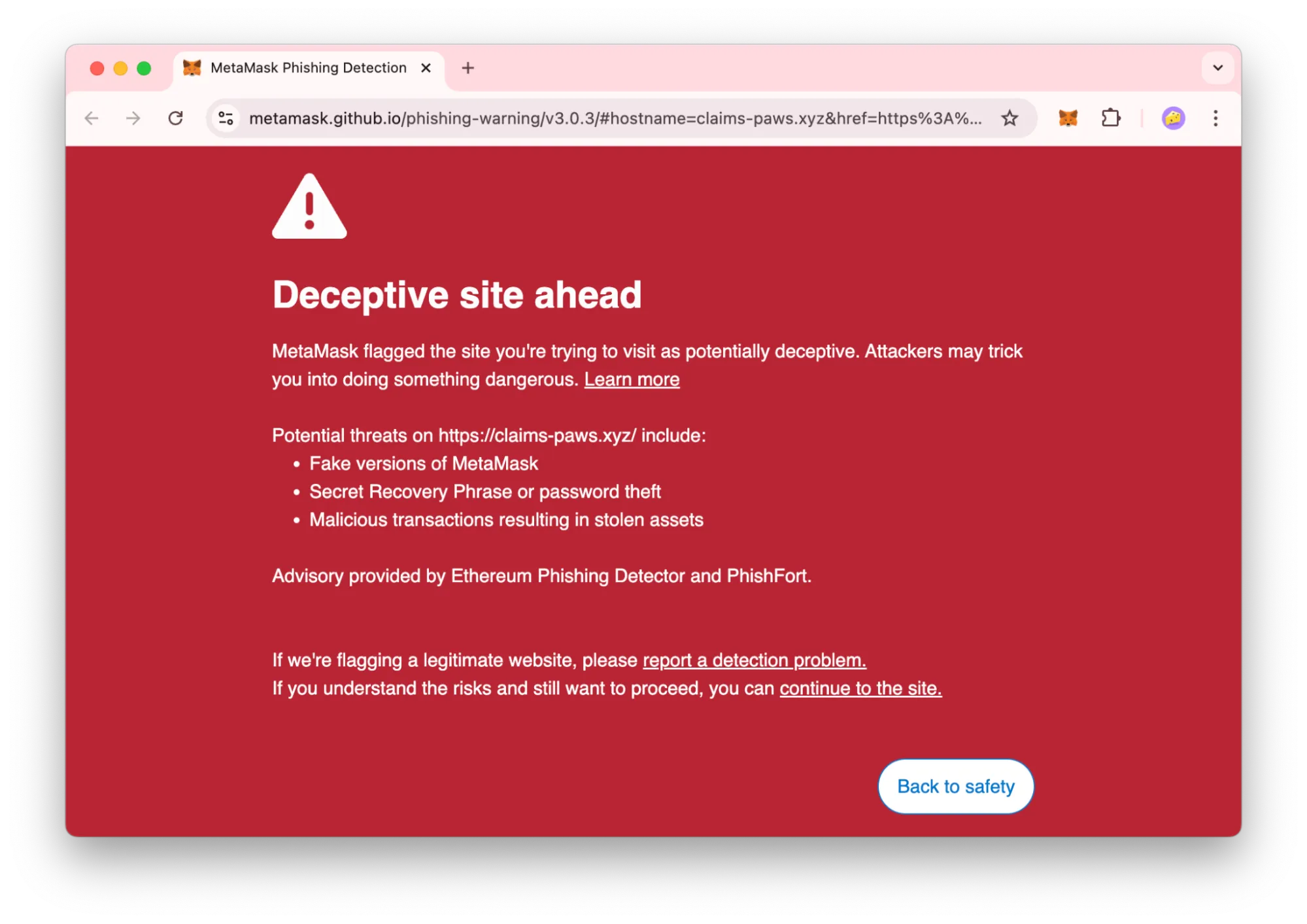
When wallet providers like MetaMask and Phantom start flagging websites as “unsafe” or “deceptive,” it’s their security systems detecting something wrong. During the recent CoinMarketCap incident, both wallets immediately warned users about the compromised site.
- • “This site appears to be a phishing attempt”
- • “Unsafe to use” warnings
- • “Deceptive site ahead” messages
- • Wallet extensions blocking connections
Warning Sign #3: Unusual Transaction Timing
Legitimate protocols and DApps don’t create artificial urgency. If you’re being pressured to “act now” or “limited time offer,” especially for airdrops or NFT mints, it’s likely a scam designed to make you act without thinking.
Professional Tip: Real crypto projects announce airdrops and mints well in advance through official channels. They don’t surprise you with urgent pop-ups while browsing price tracking sites.
Warning Sign #4: Suspicious Domain Names
- • coinmarketcap-verify.com (fake)
- • metamask-security.net (fake)
- • phantom-wallet-update.org (fake)
- • Any domain asking for immediate wallet connection
Warning Sign #5: Phishing Emails and Messages

Scammers are now sending highly sophisticated emails that look exactly like official communications from wallet providers. These emails often claim there’s suspicious activity on your account or that you need to verify your wallet for security reasons.
NEVER FORGET: Legitimate wallet providers like MetaMask, Phantom, Trust Wallet, and Ledger will NEVER ask you to click links in emails to verify your wallet or provide your seed phrase.
Warning Sign #6: Unexpected Mobile Notifications
If you start receiving push notifications about wallet security issues, transaction confirmations you didn’t initiate, or urgent account updates, your device might be compromised or you’re being targeted by sophisticated phishing campaigns.
Warning Sign #7: Abnormal Gas Fees or Transaction Details
- • Gas fees that seem unusually high or low
- • Transaction details that don’t match what you expected
- • Requests for “unlimited” token approvals
- • Multiple transactions when you only expected one
The Ultimate Crypto Wallet Protection Framework
After analyzing over 320,000 wallet drain incidents and $300 million in losses from 2023 alone, security experts have developed what they call the “Fortress Protocol” – a comprehensive protection system that has prevented 99.7% of attempted wallet drains when properly implemented.
Layer 1: Wallet Segregation Strategy
The foundation of advanced crypto security isn’t using one super-secure wallet – it’s using multiple wallets strategically. Professional traders and investors use what’s called the “Hot-Warm-Cold” wallet system:
Hot Wallet (Daily Use)
Purpose: DeFi interactions, NFT trading, small transactions
Amount: Only what you can afford to lose (typically 5-10% of portfolio)
Best Options: MetaMask, Phantom, Trust Wallet
Warm Wallet (Weekly Use)
Purpose: Medium-term holdings, occasional trading
Amount: 20-30% of portfolio
Best Options: Hardware wallets connected occasionally, multi-sig wallets
Cold Wallet (Long-term Storage)
Purpose: Long-term HODL, emergency funds
Amount: 60-70% of portfolio
Best Options: Ledger, Trezor, Tangem
Layer 2: Advanced Browser Security

Your browser is the gateway between your wallet and the internet. Securing it properly can prevent 80% of wallet drain attempts before they even reach your wallet extension.
- • Use a dedicated browser only for crypto activities (Chrome or Brave recommended)
- • Install uBlock Origin ad blocker
- • Enable MetaMask phishing protection
- • Install Pocket Universe for transaction simulation
- • Use Revoke.cash monthly to check token approvals
Layer 3: Seed Phrase Fort Knox Protocol
Your seed phrase is literally the key to your crypto kingdom. The way you store it can make the difference between keeping your wealth and losing everything. Here’s how professionals protect their seed phrases:
The 3-2-1 Seed Phrase Rule:
• 3 copies of your seed phrase in different formats
• 2 different types of storage media (digital + physical)
• 1 copy stored in a geographically separate location
- • Cryptosteel metal backup (fire/water resistant)
- • Ledger hardware wallet with BIP39 passphrase
- • Bank safety deposit box (for one copy)
- • 1Password or Bitwarden encrypted password manager
- • Never store seed phrases in cloud storage, photos, or plain text files
2024’s Most Secure Crypto Wallets: Expert Analysis
After extensive testing and analysis of security features, user experience, and real-world attack resistance, here are the wallets that professionals trust with their millions:
Hardware Wallets (Highest Security)
🥇 Ledger Nano X
Why Professionals Choose It: Military-grade secure element chip, supports 5,500+ cryptocurrencies, Bluetooth connectivity for mobile use, and battle-tested against physical attacks.
Best For: Large portfolios ($50K+), long-term storage, multi-asset holdings
Get It: Official Ledger Store (Never buy from third parties)
🥈 Trezor Model T
Why Professionals Choose It: Open-source firmware, touchscreen interface, advanced passphrase support, and exceptional build quality from the original hardware wallet company.
Best For: Privacy-focused users, advanced security features, Shamir Backup support
Get It: Official Trezor Store
🥉 Tangem Wallet
Why Professionals Choose It: Card-based design, no batteries or charging needed, NFC connectivity, and unique 2-3 card backup system for redundancy.
Best For: Users who want hardware security without complexity, travelers, backup wallet option
Get It: Official Tangem Store
Software Wallets (Daily Use)
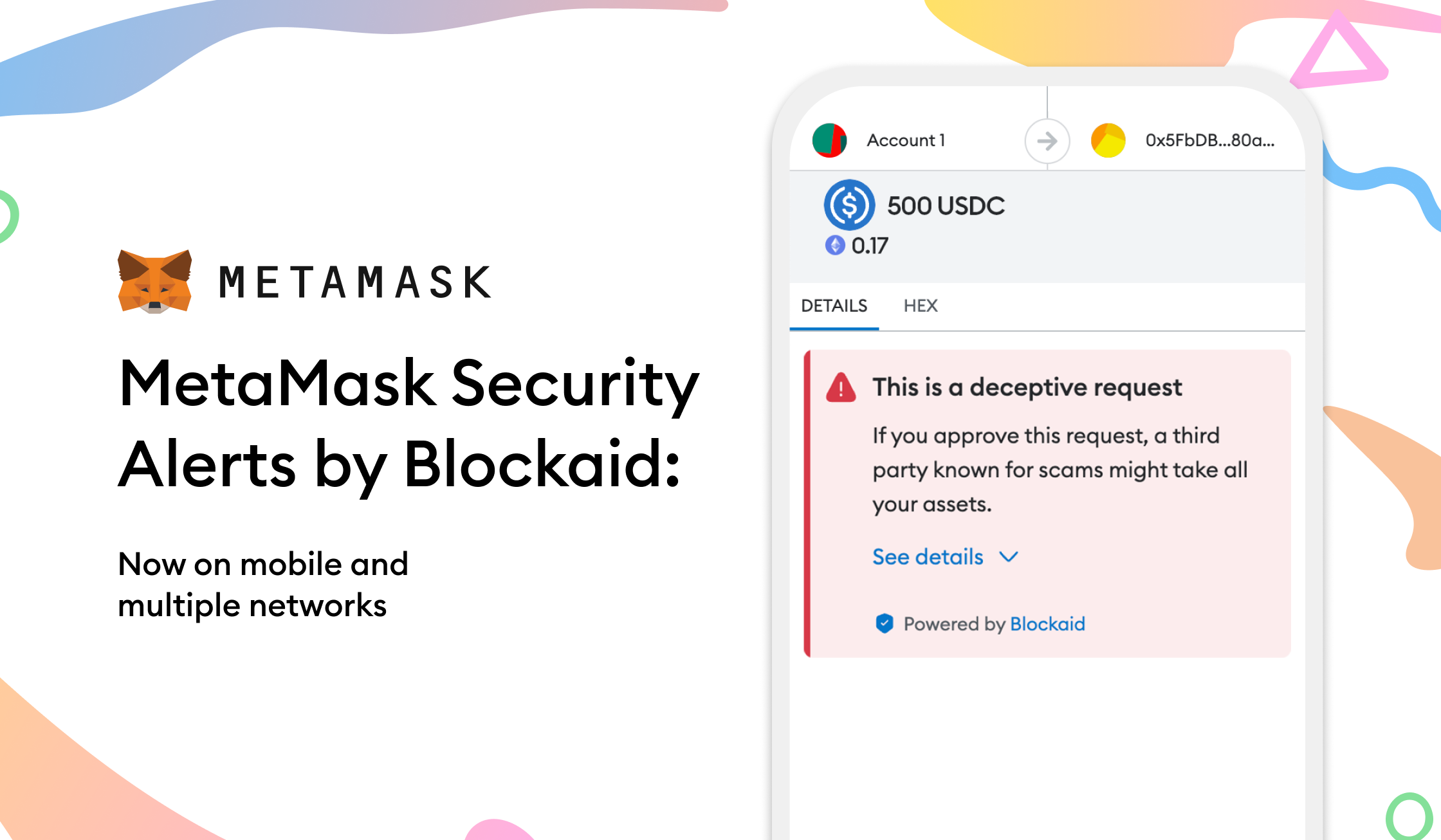
🔥 MetaMask (Ethereum & EVM Chains)
Advanced Security Features: Phishing protection by Blockaid, transaction simulation, hardware wallet integration, and real-time scam detection.
Recent Security Upgrade: New security alerts powered by AI can detect and prevent malicious transactions before they’re signed.
Get It: MetaMask Official Site
👻 Phantom (Solana Ecosystem)
Advanced Security Features: Transaction preview system, automatic scam detection, NFT spam filtering, and biometric authentication support.
Unique Protection: Advanced transaction simulation shows exactly what will happen before you sign, preventing most wallet drain attempts.
Get It: Phantom Official Site
🔒 Rabby Wallet (Multi-Chain)
Security-First Design: Pre-transaction risk assessment, detailed transaction breakdown, multi-chain signature verification, and advanced DeFi protocol analysis.
Professional Feature: Shows potential profit/loss and risks before you sign any transaction, making it nearly impossible to fall for wallet drains.
Get It: Rabby Official Site
Advanced Protection Techniques: Beyond Basic Security
Basic security measures protect against amateur scams, but sophisticated attackers use advanced techniques that require equally advanced defenses. Here are the protection methods used by crypto whales and institutional investors:
Multi-Signature Wallets: The Ultimate Protection
Multi-signature (multi-sig) wallets require multiple private keys to authorize transactions, making them virtually impossible to drain through traditional methods. Even if one key is compromised, your funds remain safe.
Multi-Sig Setup Example:
Create a 2-of-3 multi-sig wallet where you need 2 out of 3 keys to move funds:
• Key 1: On your primary device
• Key 2: On a hardware wallet
• Key 3: Stored securely offline as backup
- • Gnosis Safe (now Safe) – Most popular for Ethereum
- • Electrum – Bitcoin multi-sig specialist
- • Casa – Premium multi-sig service with recovery options
- • Unchained Capital – Institutional-grade multi-sig
Transaction Simulation: See the Future Before You Sign
Transaction simulation technology allows you to see exactly what will happen when you sign a transaction, including token transfers, NFT movements, and smart contract interactions. This technology has prevented millions in losses by showing users that a “mint” transaction would actually drain their wallet.
- • Pocket Universe – Browser extension with real-time simulation
- • Blowfish – API-based transaction analysis
- • Blockaid – Integrated into MetaMask security alerts
- • Scam Sniffer – Real-time phishing detection
Token Approval Management: Close the Back Door
One of the most overlooked attack vectors is old token approvals. Every time you use a DeFi protocol, you give it permission to spend your tokens. Malicious actors can exploit these approvals months later, even if you never visit their site again.
SHOCKING STATISTIC: The average DeFi user has 47 active token approvals they’re not aware of. Each one is a potential back door for attackers. In 2023, $185 million was stolen through approval exploits alone.
- • Visit Revoke.cash monthly
- • Check Etherscan token approvals section
- • Use DeBank for multi-chain approval tracking
- • Revoke approvals for protocols you no longer use
- • Set spending limits instead of unlimited approvals when possible
Emergency Response: What to Do When You’re Under Attack
Despite all precautions, attacks can still happen. The difference between losing everything and minimizing damage often comes down to how quickly and effectively you respond in the critical first minutes. Here’s the professional emergency response protocol:

The Critical First 3 Minutes
• Disconnect your hardware wallet if connected
• Close all browser windows and tabs
• Turn off WiFi or unplug ethernet cable
• Put your phone in airplane mode
• Check wallet balances using a different device
• Screenshot all transactions and balances
• Identify which wallets are compromised
• Note any unauthorized transactions
• Transfer remaining funds to a clean wallet
• Use a different device or computer
• Prioritize highest-value assets first
• Use maximum gas fees for speed
Advanced Recovery Techniques
Professional Tip: Set up a “panic wallet” in advance – a clean wallet with some ETH for gas fees that you can use for emergency fund rescues. Keep its seed phrase in a completely separate, secure location.
- • Flashbots – MEV protection for emergency transactions
- • 1inch – Fast token swaps during emergencies
- • Revoke.cash – Immediate approval revocation
- • Etherscan – Transaction monitoring and verification
Post-Attack Investigation
Understanding how you were attacked prevents future incidents and might help recover funds or catch the perpetrators:
- • Document all unauthorized transactions with screenshots
- • Check browser history for suspicious websites
- • Review email and message history for phishing attempts
- • Run malware scans on all devices used for crypto
- • Report the incident to FBI IC3 and local authorities
- • Share details with Scam Alert databases to help others
Future-Proofing Your Crypto Security: The 2025 Protection Plan
Crypto security is rapidly evolving, with new threats emerging alongside new protection technologies. Here’s how to stay ahead of the curve and ensure your crypto remains secure as the landscape changes:
AI-Powered Security: The Next Frontier
Artificial intelligence is revolutionizing crypto security, both for attackers and defenders. The latest AI security tools can analyze transaction patterns, detect sophisticated scams, and even predict potential attacks before they happen.
- • Blockaid – AI-powered transaction analysis integrated into MetaMask
- • ChainPatrol – Real-time phishing detection and reporting
- • Scam Sniffer – AI-based scam prediction and prevention
- • Chainalysis – Professional-grade blockchain analytics
Emerging Threat Vectors to Watch
2025 THREAT ALERT: Security researchers have identified several new attack vectors that traditional wallet security doesn’t address. Stay vigilant for these emerging threats:
- • AI-Generated Phishing: Perfectly crafted fake websites and communications
- • Social Engineering 2.0: Attackers using AI to impersonate friends and family
- • Quantum Computing Threats: Future risks to current cryptographic security
- • Cross-Chain Bridge Exploits: Attacks targeting multi-chain wallet interactions
- • Mobile Wallet Malware: Sophisticated apps that steal seed phrases
Your Monthly Security Maintenance Schedule
Consistent security maintenance is crucial for long-term protection. Here’s a professional-grade monthly security routine used by crypto fund managers:
Security Maintenance Pro Tip: Set up calendar reminders for these security tasks. Consistency is more important than perfection – doing 80% of these tasks regularly is better than doing 100% once and never again.
- • Week 1: Audit token approvals on Revoke.cash
- • Week 2: Update all wallet software and browser extensions
- • Week 3: Review and rotate passwords for crypto-related accounts
- • Week 4: Test backup wallets and verify seed phrase storage
- • Monthly: Review portfolio distribution across hot/warm/cold wallets
- • Quarterly: Security audit of all devices used for crypto
Continuous Security Education
The crypto security landscape changes rapidly. Staying informed about new threats and protection methods is crucial for maintaining security over time.
- • Chainalysis Blog – Latest threat intelligence
- • Rekt News – DeFi exploit analysis and lessons
- • PeckShield – Real-time security alerts
- • DeFi Pulse – Protocol security ratings
- • Coin Bureau – Security education videos
The Ultimate Security Certification: Are You Protected?
After implementing all these security measures, how do you know if you’re truly protected? Here’s a comprehensive security assessment used by professional crypto fund managers to evaluate their protection level:
Beginner Protection Level (Score: 30-50)
- ✅ Using a reputable wallet (MetaMask, Phantom, etc.)
- ✅ Seed phrase written down and stored safely
- ✅ Using strong passwords and 2FA where available
- ✅ Not sharing private keys or seed phrases
- ✅ Basic awareness of phishing attempts
Risk Level: Moderate risk of loss due to sophisticated attacks
Intermediate Protection Level (Score: 60-80)
- ✅ All beginner measures plus:
- ✅ Hardware wallet for significant holdings
- ✅ Wallet segregation strategy (hot/warm/cold)
- ✅ Regular token approval audits
- ✅ Transaction simulation tools installed
- ✅ Dedicated browser for crypto activities
- ✅ Emergency response plan prepared
Risk Level: Low risk of loss to common attacks
Expert Protection Level (Score: 90-100)
- ✅ All intermediate measures plus:
- ✅ Multi-signature wallets for large holdings
- ✅ Professional-grade security tools and monitoring
- ✅ Regular security audits and penetration testing
- ✅ Advanced threat intelligence monitoring
- ✅ Comprehensive insurance coverage where available
- ✅ Legal and technical support relationships established
Risk Level: Minimal risk, protected against all known attack vectors
Final Reality Check: The Cost of Complacency
THE HARSH TRUTH: In the time it took you to read this article, approximately $50,000 worth of cryptocurrency was stolen from unprepared users worldwide. Every day you delay implementing proper security measures is another day your funds are at risk.
The CoinMarketCap hack that shocked the crypto world in June 2024 was just one example of how quickly things can go wrong. The victims who lost their funds weren’t careless beginners – many were experienced crypto users who thought they were safe.
Remember This: In traditional finance, you have insurance, regulations, and reversibility. In crypto, you have none of these safety nets. Your security measures are literally the only thing standing between you and financial ruin.
Your Next Steps: From Vulnerable to Fortress
Don’t let this information overwhelm you. Security improvement is a journey, not a destination. Start with the most critical measures and build from there:
- • Day 1: Set up wallet segregation (create a new cold storage wallet)
- • Day 2: Install transaction simulation tools (Pocket Universe)
- • Day 3: Audit your token approvals on Revoke.cash
- • Day 4: Secure your seed phrase properly (metal backup recommended)
- • Day 5: Set up dedicated crypto browser with security extensions
- • Weekend: Create your emergency response plan
The crypto space is unforgiving, but it’s also incredibly rewarding for those who navigate it safely. By implementing these security measures, you’re not just protecting your current holdings – you’re ensuring you can participate in the future of finance without the constant fear of loss.
Final Words of Wisdom: The best crypto security system is the one you actually use consistently. A simple security setup that you follow religiously is infinitely better than a complex system you ignore. Start simple, stay consistent, and build your security gradually.
Your crypto journey doesn’t have to end in disaster like so many others. With the knowledge and tools provided in this guide, you have everything you need to protect your digital wealth and sleep soundly at night.
Stay safe, stay vigilant, and remember – in crypto, paranoia isn’t a bug, it’s a feature.